As part of a ‘System & Network Security’ module at University, I conducted several practical attacks within a virtual environment, and furthermore produced a risk analysis for a given scenario.
I gained experience with:
- Threat Modelling / Risk Analysis
- Cryptography (Symmetric / Public Key Exchange, Hashing, Signatures & Nonces)
- Identification, Authentication, Authorisation Methodologies (Continuous & Multi-Factor)
- Malicious Code Execution
- Firewall Rules (IP Tables)
- Web Security Protocols (CAs, SSL/TLS, IPSec)
- Privacy (GDPR, K-Anonymity)
In practical sessions, using Kali Linux for learning purposes, I exploited malicious code execution attacks such as ‘buffer overflow’ (against TLS versions), XSS (cross-site-scripting) and SQL injection. Additionally, I explored the decryption of programs, DNS spoofing and phishing scams.
To assess the theoretical underpinnings of the module, using Microsoft’s FAIR model, I identified a potential STRIDE categorisation for a hypothetical vulnerability and attack.
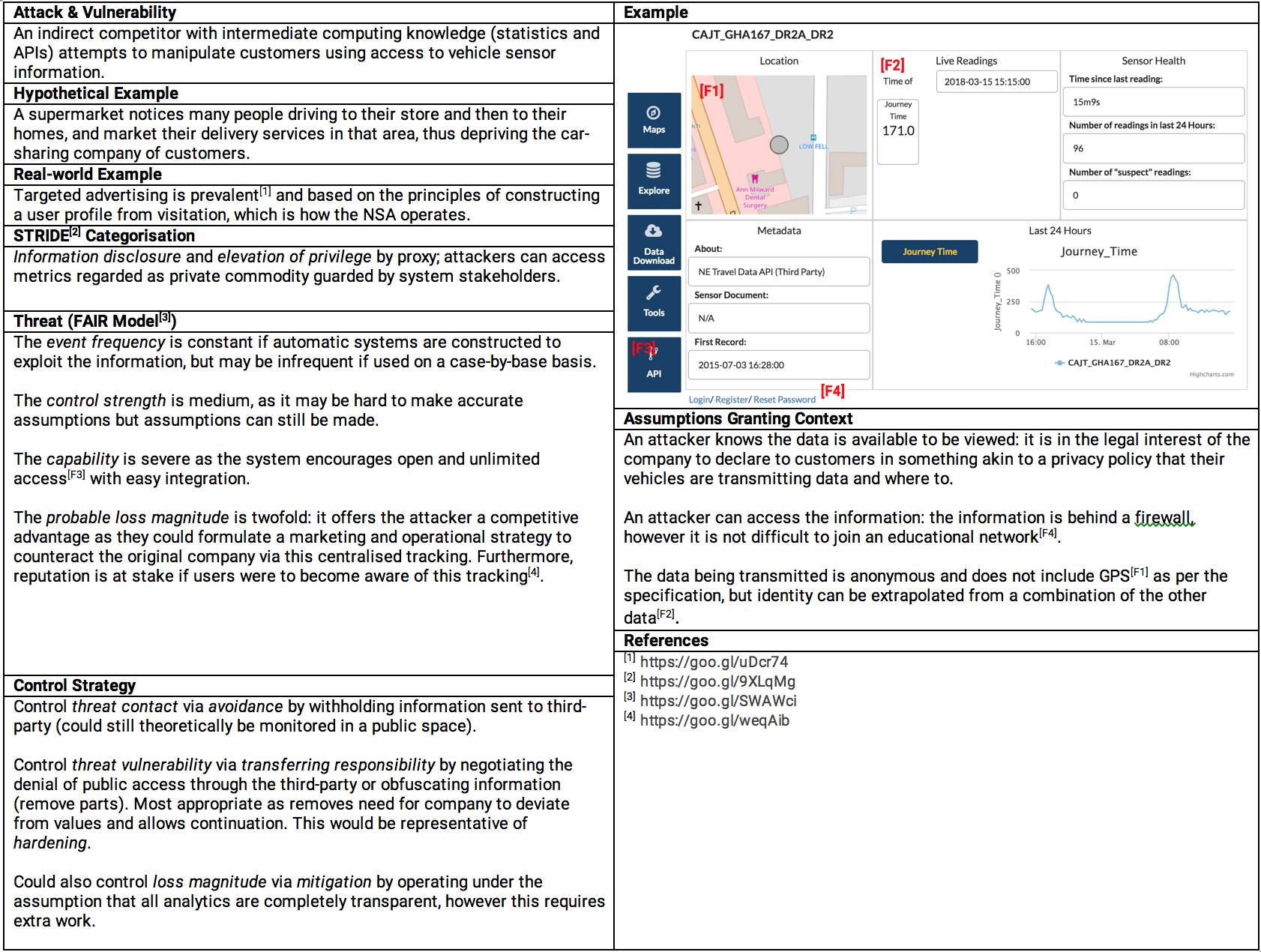
In the practical sessions, the goal was always to uncover some information, and disrupt an element of the CIA (confidentiality-integrity-availability) triad. From the perspective of somebody defending against attack, I was taught to change a user’s behaviour by altering the opportunity and motivation behind being security-conscious. Resultantly, I'm now familiar with packet-filtering rules, and role/attribute-based access-control strategies, which have enlightened aspects of previous projects that contained such elements.
Some aspects were covered theoretically, which helped provide greater context to the current state of security in-industry. During analysis of threats, the event frequency was considered, along with its capability and loss magnitude. A control strategy of avoidance and mitigation was suggested. These were placed into a lifespan that always considered the real-world implications of an attack, which ranged from mundane ‘shoulder-surfing’ to man-in-the-middle attacks against insecure/inappropriate policies.
These activities were congruent with the module’s content. By exploring topics such as the need for security, cryptography, and privacy along with their human elements, I was introduced to the need for security in many components of a computer system, along with an understanding of their practical implementation.
In future, I am confident that I can be critical of the security of my own systems, in addition to designing something that is secured appropriately.
